White Lady
Content
Warning
You need to have enabled image loading to view this document properly. Following equations and techniques are not optimized to improve readability of this document. This document also presumes some knowledge of cryptography.
This block cipher has been developed for experimental purposes, but you may use it anyway you want at your own risk. It is not patented and it is free. If you wish to use it, you should send e-mail with subject White Lady to get ready for news.
As many of ciphers this one is also based on Feistel scheme, but it uses modified
"polymorph" version. There are registers with non-linear feedback and
substitution boxes computed from hard one in this cipher. Some of the cryptographic
operations are conditioned by the content of selected password to improve resistance
against any attack, mainly brutal force one.
White Lady uses 256 bits long key, but as it is written in the next text, you can limit
the effective length of the password by the zero padding to 256 bits so that you should be
able to comply with most of export restrictions.
Integers are stored in the little endian format, i.e. format used at Intel Pentium.
Data Block
Data block is 64 bits long; i.e. it is composed from four 16 bits long words.
type TDataBlock = packed record st, nd, rd, th:word; end;
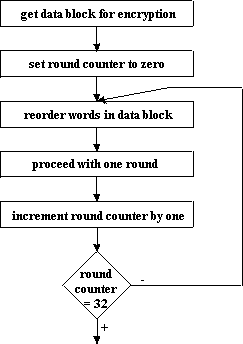
Data Block Reordering
Data block is to be reordered in dependence of password's byte at position determined
by round counter. Four most significant bits are ignored and only four least significant
bits are used this way:
If least significant bit (0x01) is set then exchange st with th.
If second least significant bit (0x02) is set then exchange nd with rd.
If third least significant bit (0x04) is set then exchange st with rd.
If fourth least significant bit (0x08) is set then exchange nd with th.
Data block is to be encrypted in one round as determined in the following figure:
This realizes "polymorph" Feistel scheme and implementation of registers with non-linear feedback. The function F usage is conditioned with the Password[(RC+1) mod 32] byte, where RC is the round counter. Indexes at F determine which bit enables usage of this function.
| Usage of Fi .. i+6 is Enabled | If |
| Fi | Least significant bit (0x01) is set to 1 |
| Fi+1 | Second least significant bit (0x02) is set to 1 |
| Fi+2 | Third least significant bit (0x04) is set to 1 |
| Fi+3 | Fourth least significant bit (0x08) is set to 1 |
| Fi+4 | Fifth least significant bit (0x10) is set to 1 |
| Fi+5 | Sixth least significant bit (0x20) is set to 0 |
| Fi+6 | Seventh least significant bit (0x40) is set to 0 |
These equations express the one-round encryption:
stnew = thnew xor stold xor Fi+3(ndold
xor Fi(stold) xor Fi+2(rdold xor Fi+1(stold)))
ndnew = ndold xor Fi(stold)
xor Fi+2(rdold xor Fi+1(stold)) xor stnew
rdnew = rdold xor Fi+1(stold)
xor ndnew
thnew = F(thold)
Function F realizes Feistel scheme with taken of substitution box. This box depends on the selected password.
The substitution box is referenced as "sbox" in this scheme. It is array with 256 elements; each is 8 bits long. Each round has different one because it depends on the round counter. Box for the first round is to be computed from the hard one, which is in ascending order from value 0 to value 255. The box for the next round is to be computed from the box of the previous round. Boxes are to be computed this way: treat this array as 2048 bits long register and rotate it left. The rotate count is to be computed this way: ((Pssw[(RC+3) mod 32] shl 8) or Pssw[(RC+2) mod 32]) mod 2048 where RC is current value of the round counter and Pssw is byte array storing password indexed from 0 to 31.
The above scheme uses four bytes from the password. They're referenced like pssw[1], pssw[2], pssw[3], pssw[4] and can be determined following way(symbols have the same meaning as in the previous clause):
| pssw[1] | Pssw[(RC+4) mod 32] |
| pssw[2] | Pssw[(RC+5) mod 32] |
| pssw[3] | Pssw[(RC+6) mod 32] |
| pssw[4] | Pssw[(RC+7) mod 32] |
To understand this section, you have to be enough familiarized with the Encryption section. Only main aspects of decryption are mentioned here.
You must know all 32 substitution boxes to proceed with decryption, because you must start decryption with the last substitution box.
Reverse function F
One-Round Decryption
Don't forget that the data block must be reordered after, not before.
Created on December 16 - 25, 1999 by Tomáš Koutný as an experimental cipher.
Updated on April 11, 2002 by Dipl.-Eng. Tomas Koutny.